MAthematical Transformations for Cultural Heritage.
///////
This page is a sub-page of our page on Asynchronous Public Service.
///////
Related KMR-pages:
• CHARGE: Cultural Heritage Asynchronous Research Grid Environment
• Modeling and Mapping
• Knowledge Negotiations
• Knowledge Manifolds
• Disagreement Management
• The Small-Mart Revolution
///////
Other related resources:
• New Narratives or Old Nightmares, by Laura Kate Gibson on Vimeo, 2015.
• Digitisation, digital interaction and social media:
embedded barriers to democratic heritage.
• Abstract service interfaces: Lessons learned from the TELL ME project.
• The Distributed Data Mesh as a Solution to Centralized Data Monoliths,
by Thomas Betts, 31 Jan 2020.
• The Four Fundamental Principles of Human-Centered Design and Application,
Essay by Don Norman at jnd.org.
• Livestreaming and museums: making museums truly accessible,
by Rebecca Carlsson, 2 March 2020, at MuseumNext.
• Time Machine : Big Data of the Past for the Future of Europe , 1 March 2019 – 29 Febr 2020.
In Swedish:
• Begreppsmodellering och matematik, Ambjörn Naeve, CID/NADA/KTH, 2001.
///////
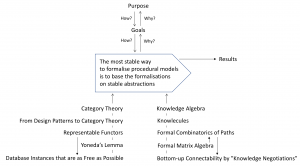
The advantage of stable abstractions
///////
The \, N_{ew} \, interface implemented through the \, O_{ld} \, implementation
\langle \, N_{ew} \, \vert \vert \, N_{ew} \, \rangle \, = \, \langle \, N_{ew} \, \vert \vert \, O_{ld} \, \rangle \langle \, O_{ld} \, \vert \vert \, O_{ld} \, \rangle \langle \, O_{ld} \, \vert \vert \, N_{ew} \, \rangle
• Foresight and hindsight process manager
\langle \, N_{ewInput} \, \vert \vert \, N_{ewOutput} \, \rangle \, = \, \langle \, N_{ewInput} \, \vert \vert \, O_{ldInput} \, \rangle \langle \, O_{ldInput} \, \vert \vert \, O_{ldOutput} \, \rangle \langle \, O_{ldOutput} \, \vert \vert \, N_{ewOutput} \, \rangle
///////
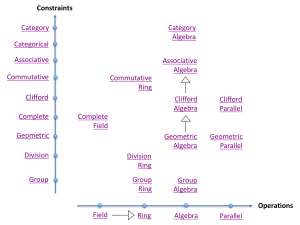
Computational layers of abstraction
///////
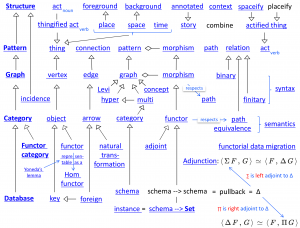
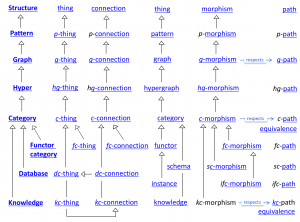
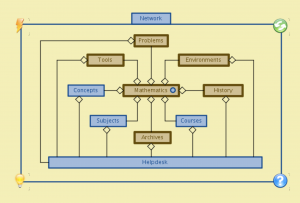
A knowlecule on math terminology:
Each non-empty box in the matrix below corresponds to a mathematical concept
that is named by concatenating the two (bold) terms in the respective row and column:
///////
“Dividing out” from structures: creating zeros by disregarding substructures:
• Ring / Ideal = Quotient ring
• Group / Normal subgroup = Quotient group
• Vector space / Linear subspace = Quotient space
• Module / Submodule = Quotient module
///////
You can’t make something from nothing.
— Aristotle
But you can make nothings from somethings
and in the world of rings
those somethings are called ideals.
— Emmy Noether
///////
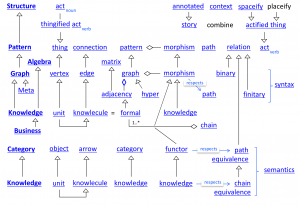
The same table with the fourth column equal to ‘calculus’ instead of ‘module’:
///////
• A powerpoint on computational levels of abstraction (version 5).
REMARK: Saving the above powerpoint and opening it on your local computer
will give you access to the explanatory hyperlinks that it contains.
///////
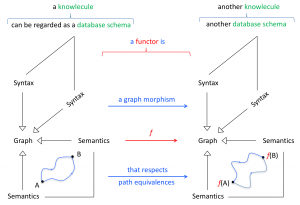
Functorial mapping between two knowlecules
///////
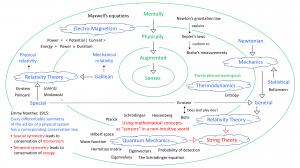
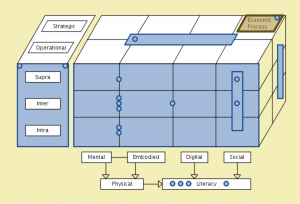
Physically and mentally augmented senses
///////
| Structure | thing | link | thing | morph | path | path equivalence |
| Pattern |
p- thing |
p- link |
pattern |
p- morph |
p- path |
p-path equivalence |
| Graph |
g- thing |
g- link |
graph |
g- morph |
g- path |
g-path equivalence |
| PowerGraph | pg-thing | pg-link | power graph |
pg- morph |
pg- path |
pg-path equivalence |
| HyperGraph | hg-thing | hg-link | hypergraph | hg-morph |
hg- path |
hg-path equivalence |
| Category |
c- thing |
c- link |
category |
c- morph |
c- path |
c-path equivalence |
| Functor Category |
fc- thing |
fc- link |
functor |
fc- morph |
fc- path |
fc-path equivalence |
|
Database Category |
dc- thing |
dc- link |
database-schema/instance |
dc- morph |
dc- path |
dc-path equivalence |
|
Knowledge Category |
kc- thing |
kc- link |
knowlecule |
kc- morph |
kc-path |
kc-path equivalence |
///////
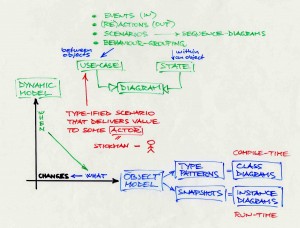
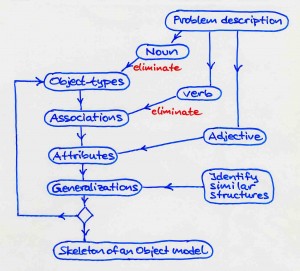
Object-Oriented Modeling (= Analysis, Design, and Implementation)
Static and dynamic models: When (dynamic) What (static) Changes:
///////
Extracting an object model:
///////
Elimination criteria:
///////
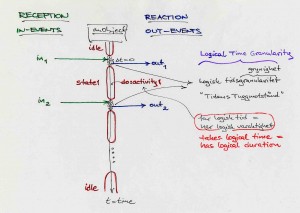
Dynamic modeling:
///////
Communication through message passing:
///////
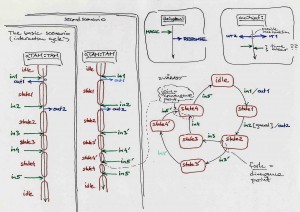
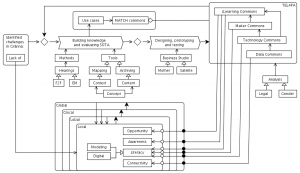
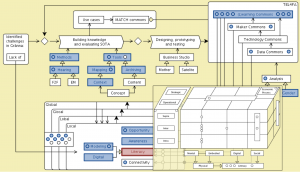
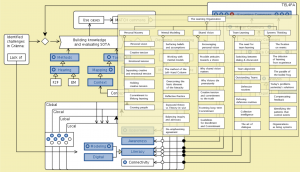
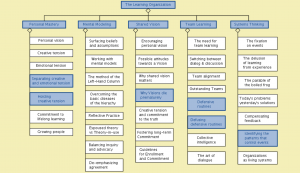
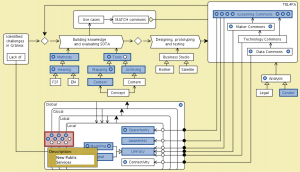
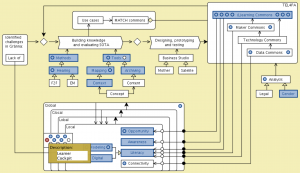
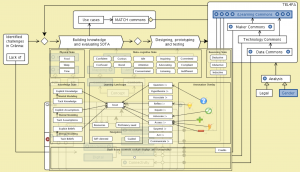
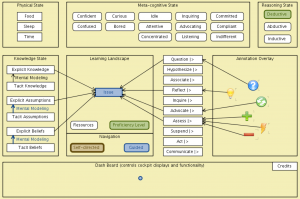
Efficacy logic:
MATCH commons:
Town 1:
Town 2:
Town 3:
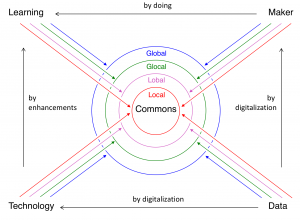
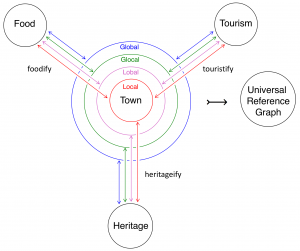
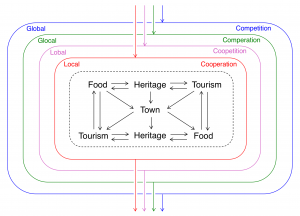
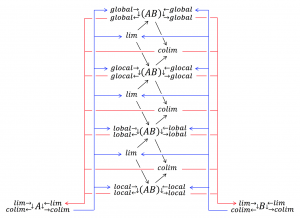
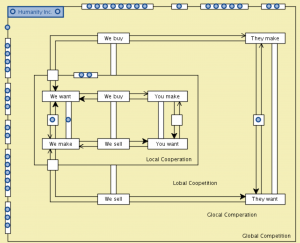
Local, Lobal, Glocal, Global Collaboraton Agencies:
///////
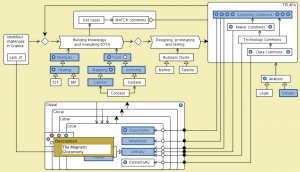
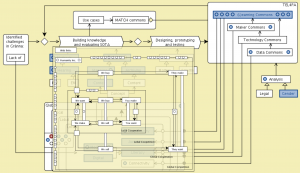
Conzilla walk-through of MATCH:
MATCH: Conzilla screenshots walk-through 1:
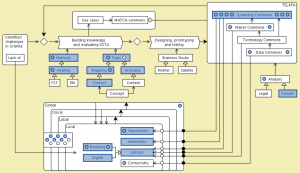
MATCH: Conzilla screenshots walk-through 2:
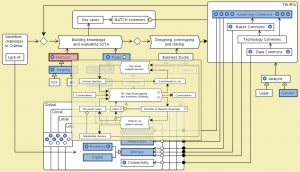
MATCH: Conzilla screenshots walk-through 3:
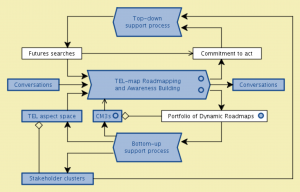
MATCH: Conzilla screenshots walk-through 4:
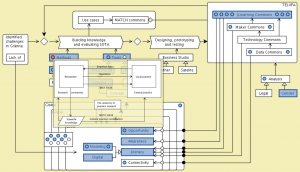
MATCH: Conzilla screenshots walk-through 5:
MATCH: Conzilla screenshots walk-through 6:
MATCH: Conzilla screenshots walk-through 7:
MATCH: Conzilla screenshots walk-through 8:
MATCH: Conzilla screenshots walk-through 9:
MATCH: Conzilla screenshots walk-through 10:
MATCH: Conzilla screenshots walk-through 11:
MATCH: Conzilla screenshots walk-through 12:
MATCH: Conzilla screenshots walk-through 13:
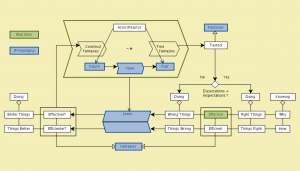
MATCH: Conzilla screenshots walk-through 14:
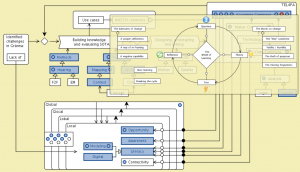
MATCH: Conzilla screenshots walk-through 15:
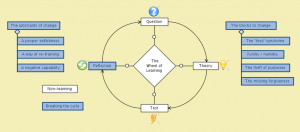
MATCH: Conzilla screenshots walk-through 16:
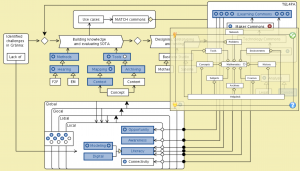
MATCH: Conzilla screenshots walk-through 17:
MATCH: Conzilla screenshots walk-through 18:
MATCH: Conzilla screenshots walk-through 19:
MATCH: Conzilla screenshots walk-through 20:
MATCH: Conzilla screenshots walk-through 21:
MATCH: Conzilla screenshots walk-through 22:
MATCH: Conzilla screenshots walk-through 23:
MATCH: Conzilla screenshots walk-through 24:
MATCH: Conzilla screenshots walk-through 25:
MATCH: Conzilla screenshots walk-through 26:
MATCH: Conzilla screenshots walk-through 27:
MATCH: Conzilla screenshots walk-through 28:
///////
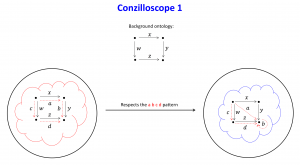
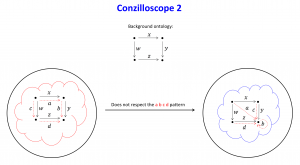
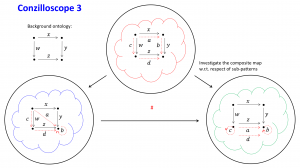
The Conzilloscope
///////
Blockchain
• Blockchain Babel: the crypto craze and the challenge to business,
Igor Pejic, KoganPage, 2019.
• Blockchain explained, Reuters infographic.
/////// Quoting Blockchain Babel, (p. 7):
Using bitcoin to illustrate how the blockchain works
To get started, every participant in the network must download the bitcoin protocol onto their computer. A copy of the bitcoin blockchain is then saved to the hard drive. By loading the program onto the new network-member’s device it is turned into a new node. Similar to the volunteer network BitTorrent, the node becomes part of a shared database. This distributed nature of the database makes it difficult for states or other regulatory bodies to get hold of such networks.
To hold and use bitcoins and other virtual currencies, users also need wallets. Misleading as it may sound, a wallet is not a physical object that holds your possessions, but is software that allows you to access your value on the blockchain. Key is a more appropriate term. Imagine a browser that enables you to enter the web. Wallets work on the same principle. The only difference is that in blockchain-based transactions the system does not identify the user via an IP address, but a pseudonymous code that no human can remember. When you transfer money to someone, your wallet sends a request to trigger a decrease of the value in your wallet and simultaneously a value increase in the other party’s wallet. The nodes – or miners as they are called in bitcoin speak – then check their respective copy of the ledger to see if the initiator of the transaction owns the necessary monetary amount. They bundle the transaction together with other reputable remittances to create a new block that is to be attached to the chain of blocks generated by past transactions. This is how the blockchain gates its name.
Now for the really clever bit, the wow factor in terms of pseudonymity and security. This is also where it gets more technically complex, so bear with me. Via another program each transaction is encrypted into a so-called ‘hash’ value that is unique and has a uniform length. Hashing simply means that the original information is transformed into a code via mathematical scrambling. This is done with one-way cryptography; so if someone only has the hash, they cannot find the initial input variables. As mentioned, each hash is unique, and it cannot be allocated to a specific transaction. Multiple hash values generated from multiple transactions are then bundled into a system called the Merkle Tree. After being bundled together, a block’s header is created. The header is a value that also includes the hash of the previous block on the chain, and this is where the chain becomes tamper-proof. Because the header of a block refers to the previous one, altering the preceding block becomes impossible without altering all the subsequent blocks (Franco, 2015). Each block is also stamped with the exact date and time, which means that no single bitcoin can be used twice (Nakamoto, 2008). Figure 0.1 shows how the blocks and the hash values are built.
The transaction is not yet completed, however. A mathematical puzzle is built around the newly generated block header, once again using the hash function. For the transactions to be verified and the block added to the chain, nodes must solve the puzzle. Here the nodes’ main service is not transaction validation; every node of the network can do that. What miners do when solving puzzles and dedicating computing power is to decide which transaction to include in each block; they have ‘the power to vote on the truth’ (Tapscott and Tapscott, 2016).
So how is this puzzle solved? This depends on the specific blockchain. In the bitcoin system, nodes do so by using brute force, i.e., they try to arrive at the right result via trial and error, plugging in one solution after the other. The possibilities for the right solution are in the trillions. Ergo, the higher the computing power, the higher the likelihood of solving the block first because nodes can plug in trial values faster – and the reward is high. The node that first hits the right solution pockets freshly minted bitcoins. Before the winning node gets the credit, however, the other miners have to verify the proposed solution. Verification can be performed quickly once you have the correct value. The nodes just plug in the value into the equation and can check it instantly. The ledger is then updated accordingly with all the transactions inside the new block. The hash that was generated on the basis of the header is saved as part of the ledger and is referenced by the next block that wants to link to the chain (Franco, 2015). In Figure 0.2 you can see a stripped-down version of the process of block generation and validation. It is important to remember at this point that the blockchain is not a store of accounts, but a list recording all transactions in its history.
This section has been dubbed ‘in computer code we trust’, alluding to the creed enshrined on US dollar bills. However, with cryptocurrencies trust is not put in God, a central bank, or any bank for that matter. The idea of a privileged authority deciding on the truth yields to decentralized consensus – this was Nakamoto’s ground-breaking innovation in 2008 and a complete conceptual shift. Yet if blockchain is going to go mainstream, the absence of authority is arguably an unsustainable concept, both commercially and technically. Commercially, you need authorities – banks, for instance – to impose the technology onto the mass market or it will stay a niche forever. Technically, no absolutely distributed system can efficiently master the crucial challenge that every payment system faces: ensuring money is not spent twice.
/////// End of quote from Blockchain Babel